We find that our participants are aware of basic general security implications, storage models, and access by others, although some of their threat models seem somewhat underdeveloped, often due to lacking technical knowledge.
Our participants have strong opinions on how comfortable they are with the access of certain parties, but are somewhat unsure about who actually has access to their documents.
Publication #
Dominik Wermke, Nicolas Huaman, Christian Stransky, Niklas Busch, Yasemin Acar and Sascha Fahl.
Sixteenth Symposium on Usable Privacy and Security (SOUPS 2020), August 12-14, 2020.
Abstract
Cloud Office suites such as Google Docs or Microsoft Office 365 are widely used and introduce security and privacy risks to documents and sensitive user information. Users may not know how, where and by whom their documents are accessible and stored, and it is currently unclear how they understand and mitigate risks.
We conduct surveys with 200 cloud office users from the U.S. and Germany to investigate their experiences and behaviours with cloud office suites. We explore their security and privacy perceptions and expectations, as well as their intuitions for how cloud office suites should ideally handle security and privacy.
We find that our participants seem to be aware of basic general security implications, storage models, and access by others, although some of their threat models seem underdeveloped, often due to lacking technical knowledge. Our participants have strong opinions on how comfortable they are with the access of certain parties, but are somewhat unsure about who actually has access to their documents. Based on our findings, we distill recommendations for different groups associated with cloud office suites, which can help inform future standards, regulations, implementations, and configuration options.
Presentation at SOUPS 2020
Downloads
| Filename | Type | Copyright |
|---|---|---|
| conf-soups-wermke20.pdf | Publication PDF | USENIX Open Access |
| survey.md | Questionnaire Markdown | - |
| soups2020-video-short-wermke.mp4 | Presentation Video | CC BY 2.0 |
| soups2020-slides-short-wermke.pdf | Presentation Slides | CC BY 2.0 |
Overview #
Office solutions are a common staple on today’s computing devices. They are so common, that you probably have no problems identifying one if not all of their app icons below:

Figure 1: Logos of common cloud office applications. Can you identify them all?
Recently, most major office providers shifted their local-only applications to online cloud platforms. The major selling points for these cloud office platforms might as well be their most concerning (security & privacy) weaknesses:
- Easy sharing of documents
- Cloud storage of data
- High similarity in design and UI to previously prevalent offline office software
And while cloud-connected office software has perks such as ease of access and sharing, it also introduces new security and privacy challenges formerly not found in their offline equivalents.
Problem(s) #
Even if you don’t use cloud office software, you are not safe from having your information processed online. Cloud-based office software is now widely used by companies, governments, and even schools.
Especially concerning is the storage of cloud data, which relates back to access rights and data safety. For example, in 2019 a German data protection commissioner banned cloud office app from schools, due to collected telemetry and potential access by U.S. officials:
“What is true for Microsoft is also true for the Google and Apple cloud solutions. The cloud solutions of these providers have so far not been transparent and comprehensibly set out. Therefore, it is also true that for schools the privacy-compliant use is currently not possible.”
— Hessian commissioner of Data Protection and Freedom of Information.
While this specific case was resolved by placing dedicated severs directly within Germany. It highlights nonetheless the changed playing field for security and privacy in the now cloud-connected office apps.
Surveys #
With our study, we wanted to investigate the following aspects of cloud office usage:
- If and how users interact with cloud office applications
- Users' awareness, perception, and attitudes are about security and privacy in cloud office apps.
- Users' understandings and basic mental models are, regarding protection, security, and access of their cloud office data.
The surveys included 9 sections ranging from general cloud office questions to personal beliefs about the responsibilities of cloud office providers:
Our survey had two versions, one in English with an US-focus, and a German-speaking version. The survey versions differed slightly due to localized answer options (e.g., localized names for government agencies) and changes to concepts that do not exist or have a different privacy implication in German-speaking countries (e.g., social security number).
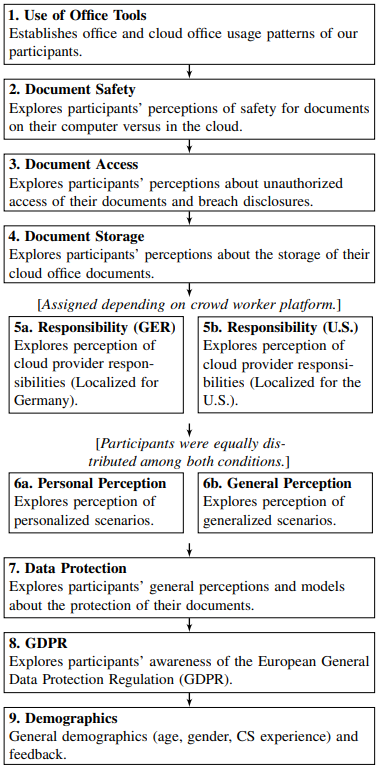
Figure 2: Illustration of the survey flow for both German and English surveys. Splits in the flow include a localized version of the ‘Responsibility’ block for Germany and the U.S. and a split for generalized scenarios vs. personalized which were randomly assigned to participants.
We pretested our survey with native speakers and additionally tested them as pre-surveys with a total of 29 participants. We conducted our surveys in mid 2019 on Amazon’s Mechanical Turk and ClickWorker, the equivalent for German-speaking countries.
Full Questionnaire
Survey
The following survey is the English version of the survey, the German version followed the same structure with nearly identical questions. Differences in questions included localization changes, e.g., for country-specific agencies and institutions. Question numbers were not displayed to the participants and order of answer options was generally randomized.
Consent Form
[Consent Form with contact information.]
Please indicate, in the box below, that you are at least 18 years old, have read and understood this consent form, and you agree to participate in this online research study.
- I am age 18 or older.
- I have read this consent form or had it read to me.
- I am comfortable using the English language to participate in this study.
- I have used cloud office software before (e.g., Google Drive or Microsoft Office 365).
- I agree to participate in this research and I want to continue with the study.
Office Demographics
For this survey, we are interested in your experience with and use of Cloud Office Suites and applications. Cloud Office Application or Online Office Application are software that can be used to create office documents in a web browser, without requiring the installation of a dedicated software. Examples for Cloud Office Suites are Google Docs/Sheets/Slides, Microsoft Office 365, and LibreOffice Online.
Q1.1: Which office suites have you used before?
(Please select all that apply)
- Microsoft Office (Offline; Word, Excel, Powerpoint, …)
- Microsoft Office 365 (Cloud-based; Word, Excel, Powerpoint, …)
- LibreOffice (Offline; Writer, Calc, …)
- LibreOffice Online (Cloud-based; Writer, Calc, …)
- Google Drive (Cloud-based; Docs, Sheets, Slides, …)
- Apple’s iWork App (Offline; Pages, Numbers. Keynote…)
- Apple’s iWork Web (Cloud-based; Pages, Numbers. Keynote…)
- OnlyOffice
- Other (please specify): ______
Q1.2: Which office suites have you used this month?
(Please select all that apply)
- Microsoft Office (Offline; Word, Excel, Powerpoint, …)
- Microsoft Office 365 (Cloud-based; Word, Excel, Powerpoint, …)
- LibreOffice (Offline; Writer, Calc, …)
- LibreOffice Online (Cloud-based; Writer, Calc, …)
- Google Drive (Cloud-based; Docs, Sheets, Slides, …)
- Apple’s iWork App (Offline; Pages, Numbers. Keynote…)
- Apple’s iWork Web (Cloud-based; Pages, Numbers. Keynote…)
- OnlyOffice
- Other (please specify): ______
Q1.3: Does your job involve using office applications on a regular basis?
- Yes
- No
- I don’t know
- I’d prefer not to answer
Q1.4: Which types of documents do you process with office suites?
For this question, please give answers both for your job and your personal life.
(Please select all that apply)
- Text (Reports, Letters, etc.)
- Spreadsheets (Numbers, Dates, etc.)
- Presentations
- Calendar and Appointments
- Emails
- Other (please specify): ______
Q1.5: How do you store your documents?
For this question, please give answers for any documents you might store, including personal and work documents, including but not limited to documents that you edit with office applications.
(Please select all that apply)
- Locally on my computer
- My office suite saves them online automatically.
- Dropbox
- Google Drive
- Network Share
- Self-hosted cloud service
- OneDrive
- iCloud
- Other (please specify): ______
Q1.6: Why do you use cloud office applications (compared to local office applications)?
(Please select all that apply)
- Provided or required by work
- Easy remote access (e.g., from multiple devices)
- Ease of collaboration
- No installation required
- Built-in backup of documents
- Free / cheap access
- Other (please specify): ______
Document Safety
Q2.1: Where do you think your documents are more secure from any unauthorized access?
[Matrix question, the scale for answers is:]
- More secure on my computer
- Somewhat more secure on my computer
- Equally secure
- Somewhat more secure in the cloud
- More secure in the cloud
- I don’t know
[The questions are:]
- Word documents
- Presentations
- Spreadsheets
- E-Mails
- Calendar and Appointments
Q2.2: Why (if at all) do you think your documents may be more secure on your computer?
[Free text field]
Q2.3: Why (if at all) do you think your documents may be more secure in the cloud?
[Free text field]
Document Access
Q3.1: Who else besides yourself might be able to access the documents you edit in cloud office applications?
(Please select all that apply)
- People I share the documents with
- My employer
- My internet provider
- The cloud office provider (e.g., Google or Microsoft)
- My browser vendor (e.g., Google or Mozilla)
- My operating system manufacturer (e.g., Apple or Microsoft)
- Cybercriminals (e.g., hackers or organized crime)
- Law enforcement or intelligence agencies (e.g., police, FBI or NSA)
- Third parties (e.g., online advertisers or plugin developers)
- The manufacturer of my computer hardware (e.g., Intel, AMD, Apple, or Lenovo)
- Other (please specify): ______
[The following 3 questions are matrix questions with the following options:]
- People I share the documents with
- My employer
- My internet provider
- The cloud office provider (e.g., Google or Microsoft)
- My browser vendor (e.g., Google or Mozilla)
- My operating system manufacturer (e.g., Apple or Microsoft)
- Cybercriminals (e.g., hackers or organized crime)
- Law enforcement or intelligence agencies (e.g., police, FBI or NSA)
- Third parties (e.g., online advertisers or plugin developers)
- The manufacturer of my computer hardware (e.g., Intel, AMD, Apple, or Lenovo)
Q3.2: Where do you think the risk is higher that the following parties can obtain unauthorized access to your cloud office documents?
- Higher risk on my computer
- Somewhat higher risk on my computer
- Equal risk
- Somewhat higher risk in the cloud
- Higher risk in the cloud
- I don’t know
Q3.3: Do you think that any of these parties have already accessed your documents?
- Yes
- No
- I don’t know
Q3.4: Please rate your level of (dis)comfort with the potential access of these parties to your cloud office documents.
- Completely comfortable
- Somewhat comfortable
- Neither
- Somewhat uncomfortable
- Completely uncomfortable
- I don’t know
Q3.5: Who do you think would inform you if an unauthorized party or person accessed you documents?
(Please select all that apply)
- People I share the documents with
- My employer
- My internet provider
- The cloud office provider (e.g., Google or Microsoft)
- My browser vendor (e.g., Google or Mozilla)
- My operating system manufacturer (e.g., Apple or Microsoft)
- Law enforcement or intelligence agencies (e.g., police, FBI or NSA)
- Third parties (e.g., online advertisers or plugin developers)
- The manufacturer of my computer hardware (e.g., Intel, AMD, Apple, or Lenovo)
- The news
- Scientists
- Nobody would inform me
- Other (please specify): ______
Q3.6: Who do you think should be responsible for informing you if an unauthorized party or person accessed your documents?
(Please select all that apply)
- People I share the documents with
- My employer
- My internet provider
- The cloud office provider (e.g., Google or Microsoft)
- My browser vendor (e.g., Google or Mozilla)
- My operating system manufacturer (e.g., Apple or Microsoft)
- Law enforcement or intelligence agencies (e.g., police, FBI or NSA)
- Third parties (e.g., online advertisers or plugin developers)
- The manufacturer of my computer hardware (e.g., Intel, AMD, Apple, or Lenovo)
- The news
- Scientists
- Nobody would inform me
- Other (please specify): ______
Q3.7: How would you like to be informed if an unauthorized party or person accessed your cloud office documents?
[Free text field]
Document Storage
Q4.1: Do you think that multiple copies of your cloud office documents exist?
These can be documents that are shared with others or private documents.
- Yes
- No
- I don’t know
- I’d prefer not to answer
Q4.2: [only shown if Q4.1 = Yes] For which purpose do you think these copies might exist?
[Free text field]
Q4.3: [only shown if Q4.1 = Yes] In which geographic locations do you think your cloud office documents and copies of these are stored?
[Free text field]
Q4.4: [only shown if Q4.1 = Yes] Which of the copies do you think are actually removed if you delete a cloud office document?
- All
- Mine and my collaborators'
- Only mine
- Only my collaborators'
- None
- I don’t know
- I’d prefer not to answer
- Other (please specify): ______
Q4.5: [only shown if Q4.1 = Yes and Q4.4 != All] Where or with whom do you think copies remain?
[Free text field]
Q4.6: [only shown if Q4.1 = Yes and Q4.4 != All] For which purpose do you think that the copies remain?
[Free text field]
Q4.7: Who do you think can delete your documents?
(Please select all that apply)
- People I share the documents with
- My employer
- My internet provider
- The cloud office provider (e.g., Google or Microsoft)
- My browser vendor (e.g., Google or Mozilla)
- My operating system manufacturer (e.g., Apple or Microsoft)
- Cybercriminals (e.g., hackers or organized crime)
- Law enforcement or intelligence agencies (e.g., police, FBI or NSA)
- Third parties (e.g., online advertisers or plugin developers)
- The manufacturer of my computer hardware (e.g., Intel, AMD, Apple, or Lenovo)
- Other (please specify): ______
Q4.8: Who do you think is responsible for protecting your data?
(Please select all that apply)
- People I share the documents with
- My employer
- My internet provider
- The cloud office provider (e.g., Google or Microsoft)
- My browser vendor (e.g., Google or Mozilla)
- My operating system manufacturer (e.g., Apple or Microsoft)
- Cybercriminals (e.g., hackers or organized crime)
- Law enforcement or intelligence agencies (e.g., police, FBI or NSA)
- Third parties (e.g., online advertisers or plugin developers)
- The manufacturer of my computer hardware (e.g., Intel, AMD, Apple, or Lenovo)
- Myself
- The US-Government
- Other (please specify): ______
Responsibility
Q5.1: Please indicate your agreement with the following statements:
[5 point-likert scale from Strongly agree to Strongly disagree + I don't know option]
- Cloud office providers should offer adequate protection for cloud office documents (e.g., by encryption and well implemented security practices)
- I should have the right to demand a full overview of my data collected by cloud office providers.
- Upon my request, cloud office providers should have to show what they do with my documents and who has or had access.
- Cloud office providers must be able to modify or delete any data they have on private individuals.
Q5.2: Please indicate your (dis)comfort with the following statements:
[5 point-likert scale from Completely comfortable to Completely uncomfortable + I don't know option]
- Cloud providers can store my documents on servers outside of the US without legal repercussions.
- US regulations and laws still apply if the documents are stored on servers outside of the US.
- US law enforcement can access my cloud documents without a court order.
- US law enforcement can force me to give up my cloud office password.
Q5.3: Where do you think the risk is higher of somebody obtaining unauthorized access to your documents if they are either stored on a server in Germany or the US?
[5 point-likert scale from "Higher risk for server in Germany" to "Higher risk for server in the US" + I don't know option]
- My employer
- My internet provider
- The cloud office provider (e.g., Google or Microsoft)
- My browser vendor (e.g., Google or Mozilla)
- My operating system manufacturer (e.g., Apple or Microsoft)
- Cybercriminals (e.g., hackers or organized crime)
- Third parties (e.g., online advertisers or plugin developers)
- The manufacturer of my computer hardware (e.g., Intel, AMD, Apple, or Lenovo)
- US government
- German governments
- Foreign government (neither US nor German)
Personal Perception
[Only scenario block A or B was randomly shown to the participants]
Scenario A - Personalized Scenario
[Question order was randomized]
Below are listed three different scenarios. How comfortable do you feel with each approach?
Q6.A.1: Your child is required by the school to use a cloud office suite for tasks. The processed documents include private information such as your child’s name and grades.
- Completely comfortable
- Somewhat comfortable
- Neither
- Somewhat uncomfortable
- Completely uncomfortable
- I don’t know
Q6.A.2: Your general practitioner uses a cloud office suite to process patient data. The processed documents include private information such as your name, age, weight, diagnosis, and treatment plan.
- Completely comfortable
- Somewhat comfortable
- Neither
- Somewhat uncomfortable
- Completely uncomfortable
- I don’t know
Q6.A.3: Your financial advisor uses a cloud office suite to process client data. The processed documents include private information such as your name, SSN, and financial information.
- Completely comfortable
- Somewhat comfortable
- Neither
- Somewhat uncomfortable
- Completely uncomfortable
- I don’t know
Scenario B - Generalized Scenario
[Question order was randomized]
Below are listed three different scenarios. How comfortable do you feel with each approach?
Q6.B.1: A school requires children to use a cloud office suite for tasks. The processed documents include private information such as children names and grades.
- Completely comfortable
- Somewhat comfortable
- Neither
- Somewhat uncomfortable
- Completely uncomfortable
- I don’t know
Q6.B.2: A doctor’s office uses a cloud office suite to process patient data. The processed documents include private information such as name, age, weight, diagnosis, and treatment plans.
- Completely comfortable
- Somewhat comfortable
- Neither
- Somewhat uncomfortable
- Completely uncomfortable
- I don’t know
Q6.B.3: A financial advisor’s office uses a cloud office suite to process client data. The processed documents include private information such as name, SSN, and financial information.
- Completely comfortable
- Somewhat comfortable
- Neither
- Somewhat uncomfortable
- Completely uncomfortable
- I don’t know
Data Protection
Q7.1: What do you think - what data does the cloud office application collect when you process documents with it?
[Free text field]
Q7.2: How do you think documents processed by cloud office applications are protected?
[Free text field]
GDPR
Q8.1: Do you know what the GDPR is?
- A data protection regulation in EU law
- A plugin for Google Drive
- A cloud office provider
- A counter terrorism act in US law
- I don’t know
- I’d prefer not to answer
Q8.2: [Only shown if Q8.1 = A data protection regulation in EU law] What do you think does the GDPR protect?
[Free text field]
Demographics
[We administered demographic questions at the end of the questionnaire to prevent stereotype bias.]
Q9.1: How old are you? (in years, e.g. 42. Optional)
[Free text field]
Q9.2: As which gender do you identify?
- Male
- Female
-
[Free text field] - I’d prefer not to answer
Q9.3: Do you have formal education (Bachelor’s degree or higher) in computer science, information technology, or a related field?
- Yes
- No
- I’d prefer not to answer
Q9.4: Have you held a job in computer science, information technology, or a related field?
- Yes
- No
- I’d prefer not to answer
Q9.5: Do you have any feedback or additional comments for us? (completely optional)
[Free text field]
After removing dropouts and filtering low-quality answers, we arrived at 200 final participants, 105 from the MTurk and 95 from ClickWorker.
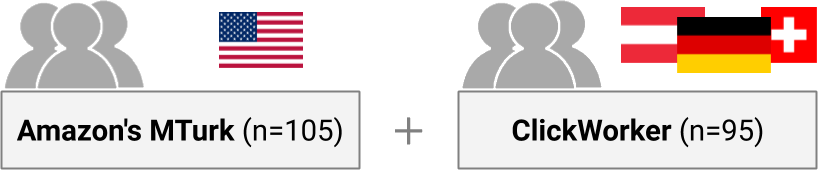
Figure 3: We conducted surveys with 200 U.S. crowd workers on Amazon’s Mechanical Turk and 95 German-speaking crowd workers on ClickWorker.
Results #
Overall, 127 participants responded to our survey on Amazon’s Mechanical Turk (U.S.) and 102 on ClickWorker (German). Of those, 105 and 95 respectively completed the survey and were considered valid for a combined total of 200 participants for whom we report results.
Use of Office Tools
The general demographics of both surveys were as follows:
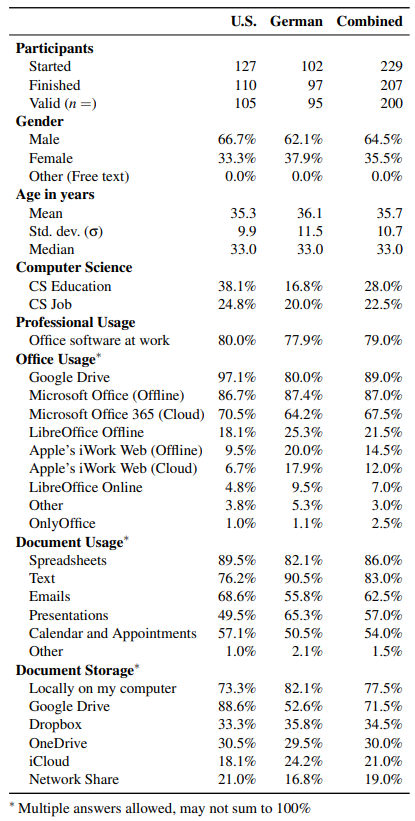
Figure 4: Demographics for all valid participants from the U.S. survey (Amazon’s Mechanical Turk), German survey (ClickWorker), and combined.
Tool Usage.
- The majority (97.1%) of our U.S. participants have used Google Drive (with its related cloud office tools such as Google Docs or Google Sheets) before, followed by Microsoft Office (Offline) (86.7%) and Microsoft Office 365 (Cloud) (70.5%).
- The majority of our German participants (87.4%) is more familiar with Microsoft Office (Offline), followed by Google Drive (80.0%) and Microsoft Office 365 (Cloud) (64.2%).
We assume this difference is likely due to the extensive, almost exclusive usage of Microsoft Office products in German businesses and government. These differences even out for office tools used in the last months where Google Drive prevails among both the U.S. and German participants (82.7%, 70.5%), followed by Microsoft Office (Offline) (50.5%, 65.3%) and Microsoft Office 365 (Cloud) (50.5%, 55.8%).
- The majority of our U.S. participants use office tools to process Spreadsheets (89.5%), Text (76.2%), and Emails (68.6%).
- As document types, the German participants process Text (90.5%), followed by Spreadsheets (82.1%) and Presentations (65.3%).
Data Storage.
- Most of our U.S. participants prefer to store their documents in Google Drive (88.6%), followed by locally (73.3%), and Dropbox (33.3%).
- While the majority of German participants prefers local storage (82.1%), followed by Google Drive (52.6%), and Dropbox (35.8%).
This mirrors the distribution of most used office tools for U.S. participants (Google Drive Office → Google Drive Storage) and German participants (Offline Microsoft Office → Local Storage).
Usage Reasons. Participants of both the U.S. and German survey agree on the top reasons why they (would) use cloud office applications over local office applications: easy remote access of documents (76.2%, 70.5%), ease of collaboration (58.1%, 59.0%), and free or cheap access (52.4%, 43.2%).
Key Findings: Use of Office Tools.
- Somewhat unsurprisingly, participants prefer to store their documents on the platform they edit them with (e.g., locally for offline office).
- Our participants agree on the benefits of cloud office applications: free access and easy collaboration for remote documents.
Document Security
We asked our participants to think about where they believe their documents are more secure from any unauthorized access, on their personal computer or in the cloud.
- Most participants reported that they feel their personal computer is more secure for storing their documents than the cloud (54.5% vs. 19.5%).
In addition to the quantitative questions, we asked our participants to explain their assessment. Most (94) of the participants who said they felt their documents would be more secure against unauthorized access on their personal computers mentioned that an attacker would require physical access to their machines to acquire access to documents, e.g., P30 said:
“You would have to physically breach my computer to get to the documents, the drive is encrypted, no one can access it." — P30
Similarly P47 explained:
“I think that documents are more secure on my computer because I’m the only one that can access them; and if there were any threats on my PC, I would use programs to get rid of them." — P47
Some participants (21) who said files were more secure on their computer thought that it was easier to attack a cloud system than their personal computer, e.g., P27 mentioned that:
“Because I know what security I have on my pc, but don’t know about Google. Of course, I assume they’ve got top of the line security, but I don’t actually know." — P27
Participants who thought documents in the cloud were more secure (39; 19.5%) mostly mentioned two reasons:
- They believe that cloud office suite providers have more security expertise than they personally do. For example,
P79 said
“The cloud is managed by big corporations. They probably take security more serious than individuals. They always have to worry about hackers so there [sic] security is likely very powerful." — P79
- Some participants assessed cloud office suites to be more “secure” than their personal computers because they have backups and losing data is less likely, e.g.,
“Local computers can be hacked and can crash. It happens. Too often, backups are not made regularly, so data can be lost in either case. With automatic backup to the cloud, documents are more secure in case of local computer issues." — P74
Other reasons for believing in a secure cloud often seem to be based on insufficient technical knowledge, e.g., “because I think it is not possible to hack the cloud." (P219). Few participants (3; 1.5%) mentioned the use of two-factor authentication and the application of encryption by cloud office suite providers as important security factors.
Key Findings: Document Security.
- Our participants seem to be aware of some general security implications of processing their documents in the cloud.
- They seem to prefer their local system in terms of security against unauthorized access, although some of their threat models appear to be underdeveloped.
Document Access
We explore our participants’ perception, misconceptions, and mental models regarding the (unauthorized) access of specific parties to their potentially sensitive documents processed in cloud office applications.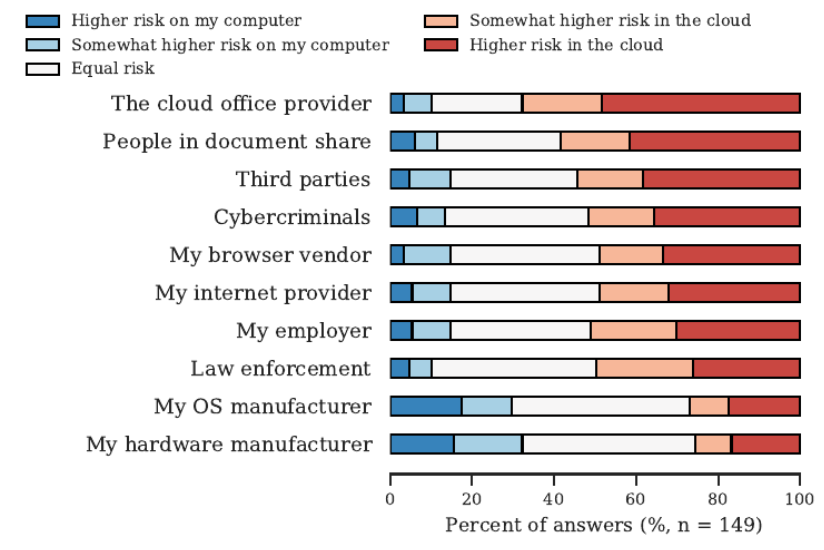
Figure 5: Likert scale for participants’ associated risk of unauthorized access between their local computer and their cloud office documents for different parties.
We found a significant difference in the risk of different parties accessing the participants documents. This might indicate that participants seem to be aware of the changed attack surface for cloud office documents and associate a higher risk of unauthorized access by cybercriminals and third parties such as advertisers and plugin developers in the cloud. These answers coincide with parties of which participants thought that they already accessed their documents, although some participants have the misconception that their browser
We also asked participants who would inform them if their cloud office documents are accessed by an unauthorized party and who should inform them. Participants’ answers point at a responsible party here:
- While the German and U.S. participants are split on the cloud office provider (73; 69.5%) and nobody (39; 41.1%) as most common answer on who would inform them respectively, both groups agree that it is the cloud office provider that should inform them (153; 76.5%).
A large number of participants explicitly told us that they like to be informed about unauthorized access of their cloud office documents by email (119; 59.5%). In addition, some participants provided us with their wishes about the information they want to receive:
"[I] [n]eed to know basically everything that the person saw. When they saw it, what they saw, where they’re from. I don’t care who gives the analysis, just that its an accurate analysis and that they let me know." — P69
Key Findings: Document Access.
- Our participants seem to have a clear idea on by whom and how they should be informed about unauthorized access of their cloud documents: the cloud office provider via (secure) email.
- Our participants seem to have strong opinions on how comfortable they are with the access of certain parties, but are somewhat unsure about who actually has access to their documents.
Considerations #
As any study with online surveys, our work includes a number of limitations typical for this type of study and should be interpreted in context.
- Generalizability. This study focuses on the responses of German and U.S. Internet users, and thus, we can offer no insight into the generalizability of results for international participants. We aimed to improve the internal validity of our study by providing localized answer options.
- Biases. Self-report studies may suffer from several biases, including over- and under-reporting, sample bias, and social-desirability bias. However, while we utilize self-report data, our central claims are not about the accuracy of respondents’ answers to a given question, but rather about the concepts and misconceptions conveyed by their answers.
- Platforms. Conducting user studies on crowd working platforms like Amazon’s Mechanical Turk and ClickWorker is a commonly used and generally accepted procedure for human-computer interaction and usable security and privacy research. While the quality of answers can suffer in a crowd worker context, we tried to ensure a high data quality by following best practices by limiting access to our surveys to high-reputation cloud workers and by manually filtering low quality answers.
- Scope. We explicitly ignored the implications of meta data collection and third party data of cloud office providers to allow participants to focus on their mental model of cloud document processing and access.
Summary #
We surveyed 200 office users from the U.S. and German-speaking countries about their experiences with and perceptions of cloud office.
Generally, participants were aware of certain security and privacy implications of writing their documents in cloud office applications, but were unaware or had severe misconceptions about others.
Overall, online office usage is quite prevalent among our participants, which often use the Google Drive or Microsoft Office 365 suites. Although the German-speaking participants still prefer offline Microsoft office by a slight margin.
Unsurprisingly, our participants prefer to store their documents on the platform they edit them with, that being in the cloud for online apps and locally for offline office software.
Our participants agree on the benefits of cloud-office software: free access without installation and easy collaboration.
Them seem to be aware of some security implications of processing their documents in the cloud, and prefer their local system in terms of security against unauthorized access. Although some assumptions regarding cloud security seem to be somewhat less developed.
In case of unauthorized access of their documents, most of our participants would like the cloud providers to inform them via email of the breach.
Recommendations #
Based on our findings, we offer recommendations for groups associated with cloud office suites:
For Office Users. A number of self-hosted alternatives to cloud office applications, such as Seafile or NextCloud, allow for most of the cloud conveniences while you retain full control of your data.
For Cloud Providers. Since our participants were somewhat unsure about who actually has access to their documents, we recommend changes to user interfaces and sharing policies that will improve their awareness.
In case of unauthorized access, we recommend notifications via email, as most of our participants prefer their provider to inform them this way. Participants also identified encryption as their preferred security measure their cloud office suite should employ for improved security.
For Researchers. Our study predates the COVID-19 outbreak, which likely makes studies investigating changed usage patterns and attitudes due to home office and lockdown an interesting area for further research.
Cite This Work #
If you want to reference this page, feel free to cite our related publication “Cloudy with a Chance of Misconceptions”:
@inproceedings{conf/soups/wermke20,
title = {Cloudy with a Chance of Misconceptions: Exploring Users' Perceptions and Expectations of Security and Privacy in Cloud Office Suites},
author = {Dominik Wermke and
Nicolas Huaman and
Christian Stransky and
Niklas Busch and
Yasemin Acar and
Sascha Fahl},
booktitle = {Sixteenth Symposium on Usable Privacy and Security, SOUPS 2020, August 12-14, 2020},
month = {Aug},
year = {2020},
url = {https://www.usenix.org/conference/soups2020/presentation/wermke},
}Wermke et al. Cloudy with a Chance of Misconceptions: Exploring Users' Perceptions and Expectations of Security and Privacy in Cloud Office Suites." Proceedings of the Sixteenth Symposium on Usable Privacy and Security. 2020.Wermke, D., Huaman, N., Stransky, C., Busch, N., Acar, Y., & Fahl, S. (2020, August). Cloudy with a Chance of Misconceptions: Exploring Users' Perceptions and Expectations of Security and Privacy in Cloud Office Suites. In Proceedings of the Sixteenth Symposium on Usable Privacy and Security.%0 Conference Proceedings
%T Cloudy with a Chance of Misconceptions: Exploring Users' Perceptions and Expectations of Security and Privacy in Cloud Office Suites
%A Wermke, Dominik
%A Huaman, Nicolas
%A Stransky, Christian
%A Busch, Niklas
%A Acar, Yasemin
%A Fahl, Sascha
%B Proceedings of the Sixteenth Symposium on Usable Privacy and Security
%D 2020TY - CONF
T1 - Cloudy with a Chance of Misconceptions: Exploring Users' Perceptions and Expectations of Security and Privacy in Cloud Office Suites
A1 - Wermke, Dominik
A1 - Huaman, Nicolas
A1 - Stransky, Christian
A1 - Busch, Niklas
A1 - Acar, Yasemin
A1 - Fahl, Sascha
JO - Proceedings of the Sixteenth Symposium on Usable Privacy and Security
Y1 - 2020
ER -
